Windows Sandbox: Your Built-In Cybersecurity Tool
Ever hesitated before opening a file or clicking a suspicious link? Or maybe you just need a quick, safe space to check something out without spinning up a full virtual machine or risking your main PC. Many Windows users already have a powerful, built-in tool designed for this: Windows Sandbox. While many are familiar with it, the real power lies in unlocking customization options using configuration files, allowing you to tailor the sandbox for specific tasks and analysis.
Windows Sandbox
Companion Video Overview
What You'll See (Video Highlights):
- How to enable Windows Sandbox in minutes.
- A live demo of using the sandbox for quick file and link testing.
- The advanced configuration options that allow for customized, isolated environments.
What Is Windows Sandbox?
Think of Windows Sandbox as a completely separate, temporary desktop that lives inside your current PC. It’s a disposable virtual computer that appears when needed and vanishes without a trace when you close it.
This tool is incredibly useful, especially for security, because:
- It’s Pristine: Every time you launch it, you get a clean Windows slate with no remnants of your previous tests.
- It’s Disposable: When you close the window, everything inside is permanently wiped. No malware persistence, no cleanup needed.
- It’s Secure: It uses hardware virtualization for strong isolation from your main system, ensuring that anything done in the sandbox does not affect your main PC.
- It’s Efficient: Forget waiting for a full VM to boot; Sandbox is lightweight and starts in seconds, perfect for quick, on-the-fly checks.
How to Get Windows Sandbox
Windows Sandbox comes included in both Windows 10 and Windows 11, but only in the Pro, Enterprise, or Education editions. To check which edition you have, press Windows + R, type winver, and press enter.
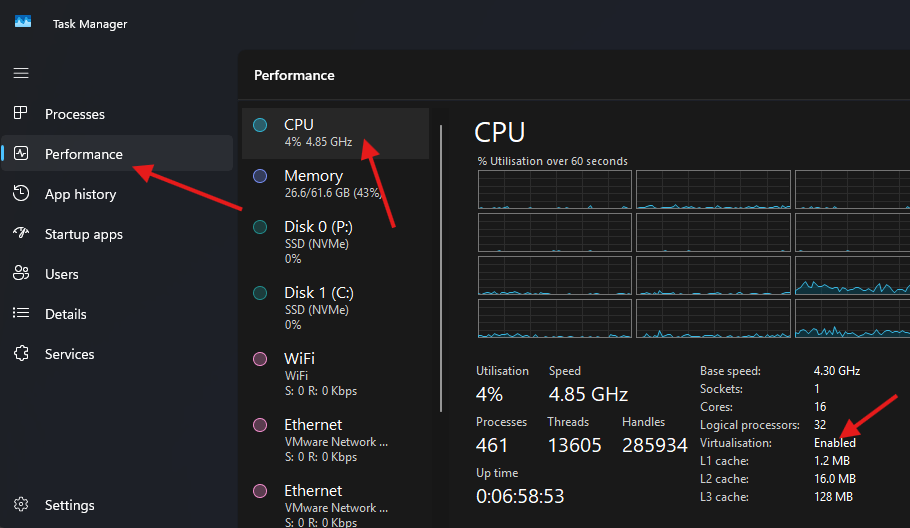
Before enabling it, you need to ensure hardware virtualization is enabled on your system. To check, open Task Manager by pressing Ctrl + Shift + Esc, navigate to the Performance tab, and check the status of virtualization under the CPU details. If it's not enabled, you will need to enable it in your computer's BIOS settings.
- Press
Windows + Rand typeoptionalfeaturesto open the Windows Features dialog. - In the list, check the box for Windows Sandbox.
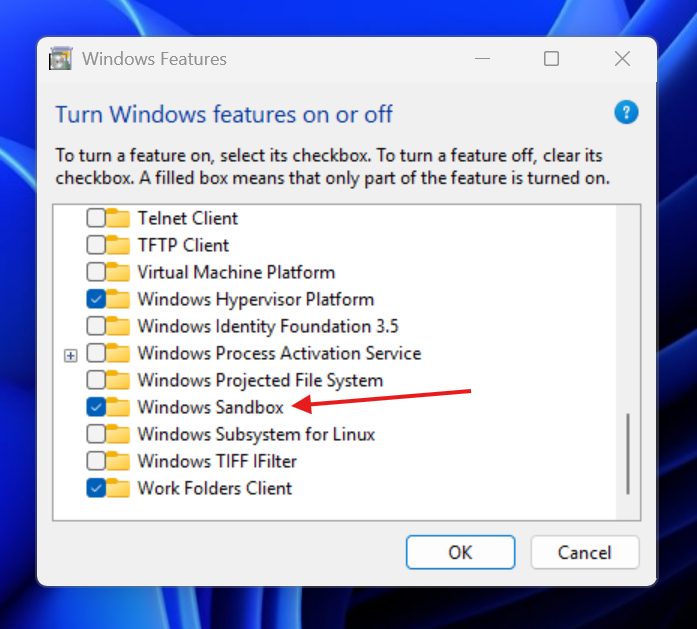
Once restarted, Windows Sandbox will be available as any other app from your Start menu.
Unlocking Advanced Customization
While the default sandbox is great, its real power is unlocked with Windows Sandbox configuration files. These are plain text files with a .wsb extension that allow you to launch the sandbox with specific, custom configurations. Instead of just clicking the app icon, you double-click your created .wsb file.
They use a simple XML format and let you control powerful settings, such as:
- Disabling Networking: A critical feature for malware analysis, this prevents the sandbox from communicating with external networks.
- Mapping Folders: You can map a folder from your host machine to the sandbox, making it easy to share files. A key security setting is to use the
ReadOnlyflag to prevent the sandbox from writing back to the host. - Running Scripts on Startup: Use a
LogonCommandto run a PowerShell script or install tools automatically as soon as the sandbox launches.
Practical Application: A Custom .wsb File
Here is an example of a .wsb file that combines these powerful features. This file maps a read-only folder to the sandbox and runs a PowerShell script to install WinGet and Notepad++.
<Configuration>
<MappedFolders>
<MappedFolder>
<HostFolder>C:\Users\YourUser\Desktop\SandboxShare</HostFolder>
<SandboxFolder>C:\Users\WDAGUtilityAccount\Desktop</SandboxFolder>
<ReadOnly>true</ReadOnly>
</MappedFolder>
</MappedFolders>
<LogonCommand>
<Command>powershell.exe -ExecutionPolicy Unrestricted -File C:\Users\WDAGUtilityAccount\Desktop\logon.ps1</Command>
</LogonCommand>
</Configuration>
And here is the PowerShell script (logon.ps1) that would be placed in the SandboxShare folder:
# Install WinGet
$progressPreference = 'silentlyContinue'
Write-Host "Installing WinGet PowerShell module from PSGallery..."
Install-PackageProvider -Name NuGet -Force | Out-Null
Install-Module -Name Microsoft.WinGet.Client -Force -Repository PSGallery | Out-Null
Write-Host "Using Repair-WinGetPackageManager cmdlet to bootstrap WinGet..."
Repair-WinGetPackageManager -AllUsers
Write-Host "Done."
# Install Notepad++
winget install --id Notepad++.Notepad++ --accept-package-agreements --accept-source-agreements
# Launch Notepad++ to confirm installation
& "C:\Program Files\Notepad++\notepad++.exe"
By double-clicking the .wsb file, you get an isolated, pre-configured environment ready for testing in just moments.
Use Cases in Your Daily Life
With or without customization, Windows Sandbox is a fantastic tool for everyday use:
- Testing Untrusted Downloads: That random free utility you found online? Run it in the sandbox first to see if it's safe.
- Safe Web Browsing: Need to visit a site you don't fully trust? Open it in the sandboxed Edge browser.
- Opening Risky Attachments: Got a weird attachment from an unknown sender? Open it in the sandbox without fear of infecting your main PC.
- Trying Out New Software: Fire up the sandbox to test new software without cluttering your main system.
Common Pitfalls
- Incorrect Windows Edition: Windows Sandbox is not available on Windows Home editions.
- Virtualization Disabled: The feature will not run if hardware virtualization is not enabled in your computer's BIOS.
Key Takeaways
Windows Sandbox is your PC’s built-in, disposable secret security weapon. It's incredibly useful for quickly and safely testing files, links, and software without risking your main system. With the added power of .wsb configuration files, you can create a truly customized environment for any security task. If you have Windows Pro, Enterprise, or Education, you should definitely enable it today.
Further Reading
- Microsoft Docs: Windows Sandbox
- Microsoft Docs: WinGet
- How to Set Up a Cybersecurity Lab with VMware Workstation Pro
Want to learn more about setting up your own cybersecurity lab? Watch the video on building a full SEIM environment with Wazuh SEIM on the channel.



